HOWTO Setup WebDAV on Mac OS X
Setting up WebDAV on Leopard
The good news is that all the bits and pieces of software that you need to run a WebDAV server on Mac OS X 10.5 Leopard are already installed. You only need to configure them correctly and turn them on. Some experience with Terminal is preferred, and you should be familiar with executing UNIX commands. Let's start!
- Start Apache. (If you haven't already) You will need to enable Web Sharing, since the WebDAV service will be provided by Apache, the web server on Mac OS X. You do not necessarily need to have a web site running, but you will need to activate and run Apache. Go to System Preferences > Sharing, and turn on the box labeled
Web Sharing .
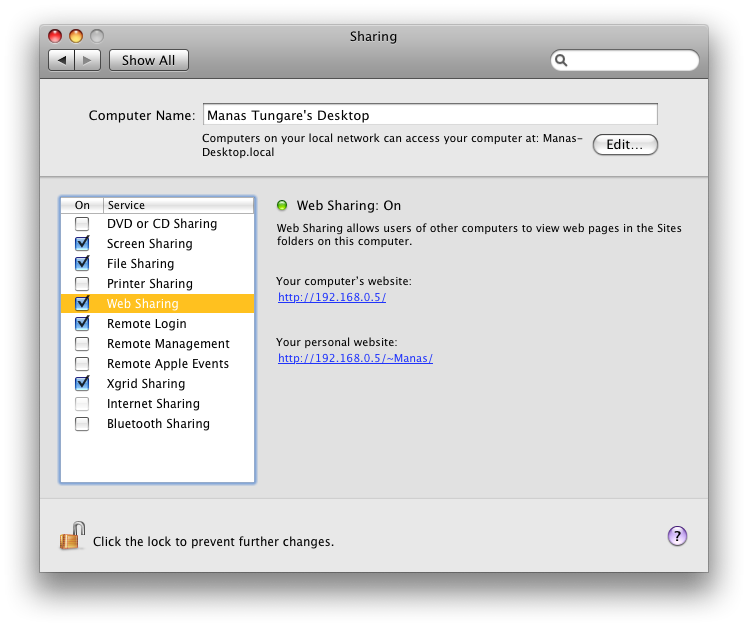
- Enable WebDAV support in Apache. Edit the file
/etc/apache2/httpd.conf, (remember to usesudoto edit it) and locate this line:LoadModule dav_module libexec/apache2/mod_dav.so
Make sure it is not commented (there should be no "#" at the beginning of the line.) Then locate this line (towards the bottom of the file):
Include /private/etc/apache2/extra/httpd-dav.conf
Again, make sure it is not commented out. It is disabled by default, so you need to remove the "#" from this line.</li>
- Configure WebDAV. Next, edit the file
/etc/apache2/extra/httpd-dav.conf. Add a section in it to create our new WebDAV share. Here's what the new section should look like. As a security precaution, you should also go ahead and delete the/usr/uploadsshare that is set by default.Alias /webdav "/Library/WebServer/WebDAV"
Free as in freedom, not as in beer
I received a request today in the mail about one of my projects that is available under a free software license. It's a web template system that I wrote to scratch a personal itch. Its hallmark feature is that it has no features, at least none that contribute to the bloat that's rampant in Drupal and Joomla and their ilk.
His email was very well-written, asking about some of the specifics of the license, and how he could undertake projects for his clients building upon my framework. After I wrote a detailed reply to him, it seemed like a good idea to post it to my blog, for there are many who're not particularly clear on how free software licensing works.
I want to use your templating system to build static websites for personal and commercial projects. I don't have lots of money so I can't promise much now but later if I will be able to make any money I will happily donate for this project.
[...]
I like open source projects because it is fun to learn how magic happens. I don't want to use your code without permission because I just personally don't think it is right thing to do. I have no problem giving you credit for this system but I need your permission to use it for commercial use?Sincerely,
[redacted]
And my reply:
Hi [redacted],
I'm glad you found the site and my projects interesting and useful, and thanks so much for writing back to let me know!
I think free software is a great way to learn and understand other people's code, that's why almost all of my projects are open-source with the license to tinker and play. All I ask in return (via the Creative Commons license) is attribution back to me if you use it in a project. I've licensed this as an Attribution-ShareAlike-Noncommercial license, so you're free to use it as you wish in any personal project as long as it is non-commercial: e.g. for an organization you belong to, or an academic department or program.
Things get a little more interesting when money enters the picture. While I'm not doing this (releasing my software) for the express purpose of making money from it, it does not seem right to me that someone else benefit financially from my work with no benefit to me. So, I politely ask that if you're planning to use this commercially, you should contact me for a separate license (the code will then be dual-licensed, and you can pick either the paid commercial license, or the default un-paid non-commercial one.)
You don't have to pay anything right away, and can play with the code as much as you want. But when you bag a client who wants to use a system based on my code, we can talk about royalties. That way, you retain the freedom to examine and modify my code as well as get a paying client, and I do not feel that someone has taken undue advantage of my generosity. This is how the open-source model was intended to work, and the free really refers to freedom, not free as in no-charge.
I'm glad you contacted me to check for permission first, and I got the opportunity to clarify. Often it's quite tricky, and lots of people have lots of misunderstandings about how free software licenses work.
Regards,
Manas.
SSH Port Forwarding on Mac OS X
After spending about an hour configuring what should, in theory, be a simple matter, I figured I’d write a blog post that might one day save another soul an hour or so from his or her life. So, for good karma, basically. In the past, I have set up port forwarding on Linux, Mac OS X and Windows, so I was a little worried that it took me about an hour trying to appease the SSH deities (and daemons).
Readymade luggage kits for baggage-less air travelers
Now there's a business opportunity that today's airline industry and airports have created: why not sell pre-packaged suitcases at airports to scalp travel-weary passengers whose luggage has landed in Murmansk?
Here's how it would work: I'd walk up to the Lost and Found desk of the airline, usually fortified behind several layers of arrows pointing upward, downward, or in all other sorts of directions in which I cannot walk; barriers laid down with those flexible tapes that you can simply unhook and pass through; or behind a scruffy-looking bouncer. They would then cheerfully inform me that my luggage has, indeed, failed to follow me around in my travails around the world, and make me fill out a 3-page form describing my "small black bag" in as many words. After a state of shock, worry, desperation, and finally, anger, I would quit discussing this with the airline folks and move on, resigned to my fate.
That's when I would notice the conveniently located "Missing Luggage Mart". I'd turn to the enterprising store-owner and tell him/her my size, and the duration of my trip. He/she would whip out a readymade suitcase of shirts, t-shirts, trousers, undergarments, socks, shorts, a belt, a cellphone charger, a toothbrush, a toothpaste, a tiny bottle of shaving cream, a tiny bottle of shampoo, etc., and I would be on my own merry way.
And a towel, of course. Nobody should ever be without their towel.
Separating Phone Numbers from Phones
Last night, I left my cell phone in my car. As with most of my follies, I realized it a few oh-no-seconds after I got home, but only after I'd taken off my jacket, gloves, cap, shoes and socks. It was an unnecessary walk in below-zero temperatures, but it got me thinking about phones, identities, what's wrong about it all, and how it could be made better.
The problem is this: phones and phone numbers are tightly coupled together [1]. No wonder people keep their phones close to their heart -- their personal identity is locked in it. If I don't carry my phone, there's no way to answer calls that I receive at that phone number. I can perhaps check voicemail from another phone, but still cannot make and receive phone calls under my own phone number.
Now compare this to email: if you go on a vacation without your own laptop computer, it is still possible to "borrow" someone's random computer and check your messages. The messages you send will have your ID (your email address) attached to them, and the people you interact with will have no idea what machine you used (and there is no need for them to know.)
Why can't we have a phone identity (our phone number) separate from the device (our phone) that is used to access it? If I forget my phone in the car overnight, I should be able to just add my phone identity to the home phone. That way, all calls that would have been received by my handset in the car will now be received at my home phone, and callers/callees will not know a thing. The next morning, I would re-establish my identity on my cell phone, and things will be back to usual.
I'm not a big fan of call redirects: that puts a temporary bandage on the problem instead of actually solving it. I don't want my identity routed to another identity: I want to be able to use my own identity wherever.
This would also open up the market for multiple-identity phones. A couple can add both their identities to a single home phone in the evening, while they carry individual cell phones during the day. Forgot your cell phone at home? No problem, just borrow a loaner phone from the office receptionist and use it all day long (just as you would borrow a loaner security badge if you forgot yours). It would also make it easy for a group of people to be able to respond to a single phone call, e.g. despatch services for emergencies. A group of doctors could share a single phone number. Whoever is on emergency call duty would add the group phone number to his/her cell phone, and remove it after the duty ends.
Historically, a phone number has been tied to a phone, mostly because of technical constraints, beginning with the days of the human-operated telephone exchange. Email has shown that identities (email addresses) can be independent of devices (computers), that many identities can share a device, and many devices can be used by a single identity.
It's an easy conceptual step forward to move to the many-to-many model instead of the current one-to-one. But there is a tremendous amount of change required of the infrastructure, and it won't be cheap. But since I don't happen to be in the business of implementing it (at least not yet!), so I'll just write about this idea and hope that someone picks it up. Maybe someone will listen, and like it, and implement it.
Then I won't have to walk out in the $#@*%$#^ snow to fetch a %$#%#$* cell phone.
[1] The more pedantic among us will point out that GSM phones keep the user's identity on a SIM card, and CDMA phones maintain a single ID tied to the IMEI number of a phone. Although possible, that does not make swapping identities across phones easy: in the first case, you must have your current phone handy, which does not help solve my problem of having left the phone in the car overnight, and the second one requires a long phone call to the carrier to make the change. Neither is as quick or handy as the method I envision.